HTB - Delivery
Delivery
Contents
Write Up
First scans show two open ports, 22 and 80. Opening up the address in a web browser brings us to a welcome page with a link to a helpdesk subdomain(http://helpdesk.delivery.htb/) and a “Contact Us” button. To access this subdomain, I added it to my hosts file with the box’s ip.
The subdomain takes us to a support ticketing portal powered by OSTicket. Searching exploit db shows a few useful exploits for OSTicket, but we still don’t know the version number. After spending some time exploring the helpdesk portal, I didn’t find any more useful information and head back to the main page to make sure I didn’t miss anything.
Back on the main page, the contact us button reveals the information we need. It also reminds us of the importance of scanning all ports during recon by providing a link to the MatterMost service running on port 8065.
For unregistered users, please use our HelpDesk to get in touch with our team. Once you have an @delivery.htb email address, you’ll be able to have access to our MatterMost server.
The MatterMost server only allows emails in the delivery.htb domain to make accounts, so we need to get one. When a new ticket is created on the helpdesk an email is also created for that ticket. Anything sent to that email is added to the ticket. Using the generated email, we sign up for an account on the MatterMost server. A verification email is sent to the address, which pops up on helpdesk ticket, allowing us to verify the new account.
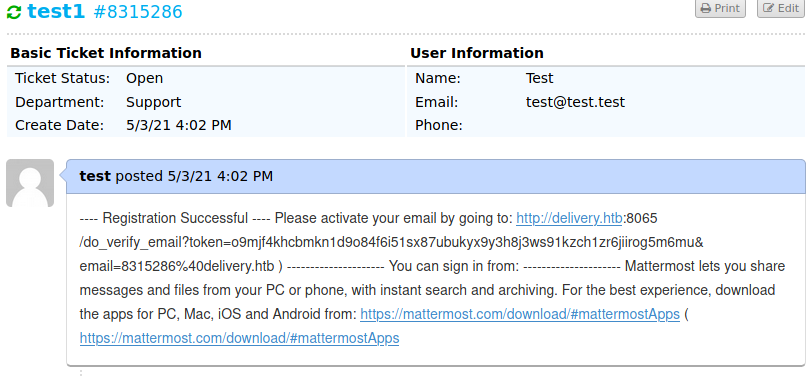
Now we have access to the MatterMost interface. After joining the “Internal” channel we immediately see a message from root:
@developers Please update theme to the OSTicket before we go live. Credentials to the server are maildeliverer:Youve_G0t_Mail! Also please create a program to help us stop re-using the same passwords everywhere…. Especially those that are a variant of “PleaseSubscribe!”
So, now we’ve got the password for the OSTicket agent portal and we know that variants of “PleaseSubscribe!” are being used as passwords across the site. Heading back to OSTicket, clicking sign in and then the link by “I’m an agent” takes us to the login page where we can use the maildeliverer credentials.
Looking through the OSTicket platform, the only other user besides the generated ones is named “bob”. With no other leads, I try the maildeliverer credentials with SSH. Success! The user flag is in the maildeliverer’s home directory.
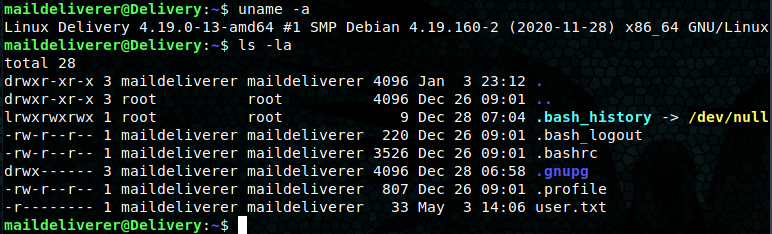
After looking up information on where OSTicket database information is stored, I learned the credentials for the storage database are located in the /include/ost-config.php file. Also, the credentials for the MatterMost db are in the /opt/mattermost/config/config.json file.
ost_user : !H3lpD3sk123!
“DataSource”: “mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTim eout=30s\u0026writeTimeout=30s”
The password to the MM database is a little hint telling us to crack the MM Admin Password.
mysql -u mmuser -p mattermost
SHOW TABLES;
SHOW COLUMNS FROM Users;
SELECT Password FROM Users WHERE Username = 'root';
+--------------------------------------------------------------+
| Password |
+--------------------------------------------------------------+
| $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
+--------------------------------------------------------------+
Okay, now that we’ve got the hash for the admin password, it’s time to crack it. Earlier we learned that variations of “PleaseSubscribe!” are being used as passwords, so we’ll combine that with a rule in hashcat to test for permutations. After a few minutes, hashcat pops the password.
hashcat -a 0 -m 3200 hash.txt passwords.txt -r OneRuleToRuleThemAll.rule
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
Session..........: hashcat
Status...........: Cracked
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
This password doesn’t get us root SSH access, but using su from the maildeliverer user works just fine!
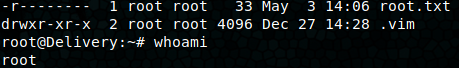
Recon
Initial Scan:
nmap -sV 10.10.10.222
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Second pass(all TCP ports):
nmap -sV -p- 10.10.10.222
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http nginx 1.14.2
8065/tcp open unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Credentials
Host users:
root : PleaseSubscribe!21
maildeliverer : Youve_G0t_Mail!
MatterMost:
(Generated) 8315286@delivery.htb : P@ssw0rd_101
root@delivery.htb
OSTicket Backend
maildeliverer : Youve_G0t_Mail!
OSTicket MySQL Database:
ost_user : !H3lpD3sk123!
General:
PleaseSubscribe! variations